Confidentiality

Confidentiality is the avoidance of the authorized disclosure of information.
-
It involves the protection of data, only providing access for people
who are authorized.
The degree of confidentiality determines the secrecy of the information.
Methods to Ensure Confidentiality
Encryption
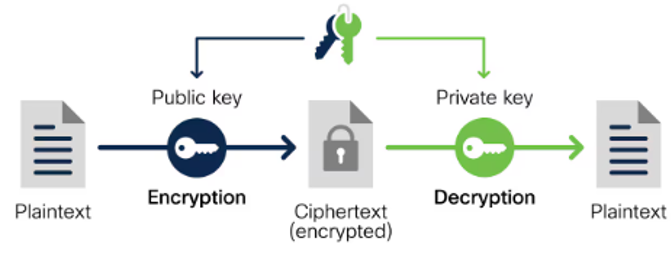
Encryption is the transfer of information using a secret encryption key, so the info can only be read using another key (the decryption key).
Authentication
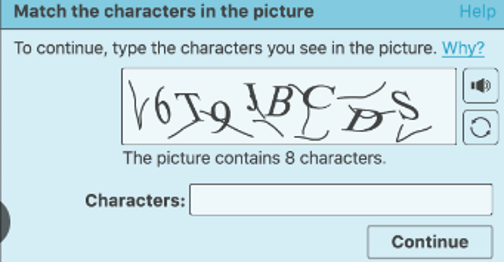
Authentication is the determination of the identity that someone has to decide whether access should be provided.
-
Ex: Google bot checker, verification codes, passwords, etc.
Physical Security

Physical security is the establishment of physical barriers to limit access to protected computational resources.
-
Ex: Windowless rooms, disallowing unknown signals to enter the
enclosure (common measures of server rooms).